If your AD account has the “User must change password at next logon” option enabled:
and you try to logon to a RDP session (with correct credentials):
you might encounter this error message:

“You must change your password before logging on the first time. Please update your password or contact your system administrator or technical support.”
This is a classic catch 22 issue: You have to logon to change you password, but you cannot logon until you’ve changed you password.
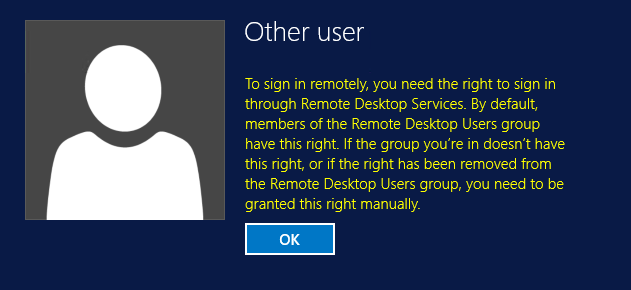
If you have access to a “normal” network connected Windows client you can change the password that way, but what if you only have RDP access?
Client side
Well, if the server allows it, you can temporary disable “Credential Security Support Provider (CredSSP)” in the RPD client. This disables Network Layer Authentication, the pre-RPD-connection authentication, and therefore enables you to change your password via RDP. CredSSP is enabled by default in the RDP client on Windows Vista and forward.
There is no option to disable CredSSP in the RDP client, so here is how you have to do it:
- Start mstsc.exe
- Click Show Options
- Click Save As
- Call it ChangePassword.rpd (or anything you’d like, but avoid the name Default.rdp)
- Open the saved ChangePassword.rpd in Notepad
- Add a new row at the end with the following text:
enablecredsspsupport:i:0
- Save the rdp file
- Double-click the rdp file
- Enter the name/IP of a domain connected computer with RDP enabled
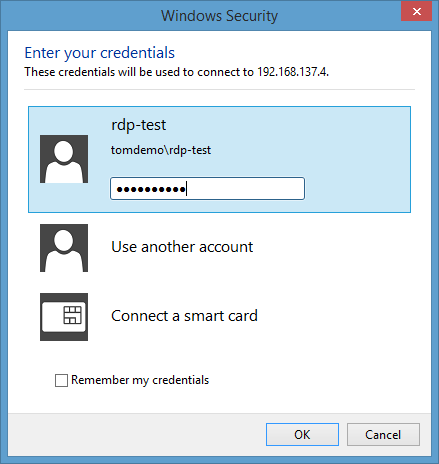
Instead of the local Windows Security prompt (the second image in the blog post) you should see a Windows Logon screen on the remote computer (if not, read on anyway):
If the account you log on with at this point has the “User must change password at next logon” option enabled, you get notified about that:
By clicking OK you get the possibility to change the password (yay!):
After changing the password you get confirmation about the change:
Clicking OK logs you in.
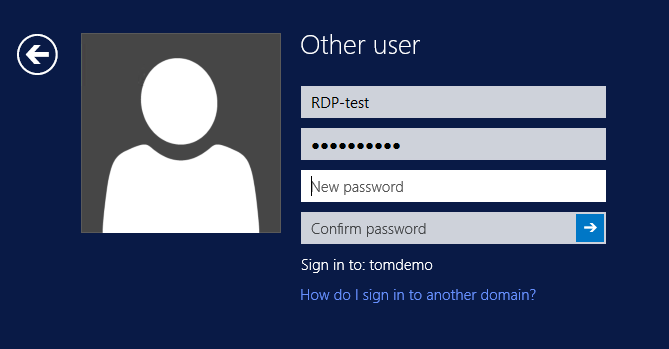
In fact, you do not need to have access to sign in through RDP, in that case this shows up, but only after you successfully changed your password:
Delete the ChangePassword.rdp file when you are done (or at least do not use it until you are forced to change your password again), since disabling CredSSP lowers the security of RDP connections.
If the server requires CredSSP
If the server does not allow you to disable Credential Security Support Provider, you get this error message when connecting:
In that case, try connecting using the FQDN (DC01.tomdemo.se and not only DC01) or connect to other servers that might allow you to disable CredSSP. As I mentioned above, you don’t have to have access to actually logon to the server.
Server side
You can also disable CredSSP on the server side, but since that lowers the security on all RDP connections to that server it is not recommended.
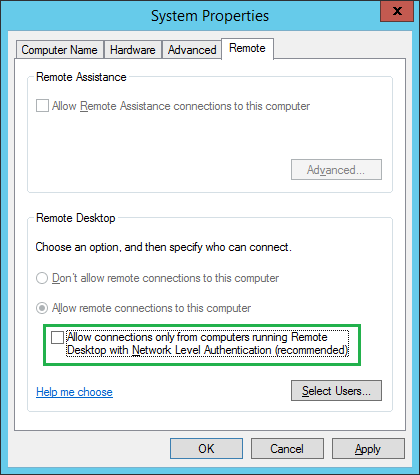
If you chose to do this anyway, you do it either by de-selecting “Allow connections only from computers running Remote Desktop with Network Level Authentication (recommended)” in System Properties:
Or if you run the Terminal Server Role:
- Open Terminal Server Configuration
- Open RDP-Tcp configuration page
- On the General tab, set the Security Layer to RDP Security Layer
Note that if you already have an existing access to a server (with the account you need to change the password with) you could just change your password in that session by pressing Ctrl-Alt-Del (or Ctrl-Alt-End in an RDP connection) and choosing Change a password:
I hope this post helped.










This worked for me. Problem was in trying to allow User Role access to my Server Windows Instance; wasn’t able to get them to authenticate by logging in. I believe that the blocker was the checkbox on System Properties “Allow Connections from Computers running Remote Desktop with Network Level Authentication” ; upon unchecking it, new users accounts could login by changing password assigned by Sys-Admin.
This worked for me! Thanks for your help! The blocker was that the option “Allow connections from Computer running Remote Desktop with Network Level Authentication” was checked. Upon unchecking, new user accounts that i had created were able to login to the instance.
Sure as hell, you are lowering you security, if you do not require NLA from clients. I would not pass this in security audit. This is flaw of the Microsoft OS architecture. Last known password should be employed to mandatory hold into sandbox of password change screen, until password updated, just like it flows in local access. All the bag of tricks to try is worth nothing for single feature missing in design.
I agree that NLA
should
be required everywhere. That being said, this “trick” has helped me and many others where that is not the case yet.
What if I were to set up a dedicated server that does not require NLA , and deny logon for Everyone, and use that as a remote password change host. Would that pass a security audit?
Tom, another trick? If you host RDP-without-NLA server, for auditors you do not deliver there outright. Then, if you deny logon, why password change should be served by the system? For abuser to be able of resetting passwords, if they can’t logon on your behalf? I do appreciate search for at least some fragile paths how to get around issues, but it makes sad, that engineers of today do not stick to the foremost principle in our field: do the right thing. Which is, to deliver feature of the system properly, instead of focusing on hackable workarounds. It is about consistency, which will support engineer himself, in the long run. Cheers.
Security is not black or white, it is – and will always be – gray. What exactly is “the right thing” for any given issue? Right for Security, IT, end-user or finance department? Secure, user-friendly, affordable. Choose any two. Why allow RDP at all, maybe require physical presence?
I often compare security with a cars. Seatbelt doesn’t always work, but still use it (is seatbelt a workaround?). Also have an airbag. Drive sober and alert. Regularly test the car. Require drivers to take a test. Not driving at all would be safer (is that the “right thing” here?), but that might not always an option.
Sorry for the rant, I often have this discussion with customers. But I thing we agree in general 😀
Tom, when we say right thing, we mean all the constellation of the engineering sense.
Engineers are not that disturbed at all.
it is good because it work, because it helps, because it resolve this issue that wasdesigned and not tested 😉
Maxim, you are either from Russia, or, less probable because of the name, from China. Proceed from this.
Eu fiz todos estes testes e nada funcionou comigo, para resolver eu abrir o atalho da conexão remota do usuário editei com o bloco de notas e na linha NEGOTIATE SECURITY LAYER estava setado como 1, marquei 0
THANKS A MILLION. This was a life saver for me. I changed the Administrator password on a remote machine (very remote) and it seems I accidentally checked the “user must change password” option. I practically locked myself, the only admin, out.
Glad it helped 😀
What do to when NLA is required, user must change password checkbox checked and that was only one Admin Account in Domain ? How reset password ? any powershell tricks ?
Thank you so much. It worked for me (saving rdp file with another name and adding the last line)
Glad i helped!
Excelente !!!
Worked ! Thank you very much
This is better, no need to lower security …
([adsi]’WinNT://domain/username,user’).ChangePassword(‘oldpassword’,’newpassword’)
Interesting, but this requires you to be authenticated with the account (to have permission to run that command) and also have line-of-sight to a Domain Controller, right?
Sure, we are talking about domain account, meaning that you need have access to domain controller. It is the same for you steps, if you want to change password on domain account. No need to be admin account locally. Just you need to know your old or newly set password.
Pingback: force password change on next login Page Info & Instructions Online User Account Activation - Odollars
Guys, PLEASE, who knows anything about the farm, absolutely:
1. Doesn’t work with policy: network level authentication – disabled, restarting the desktop id service.
2. Doesn’t work with tsconfig.msc on ALL machines in the farm setting protocol: RDP instead of NLA (negotiation), restart desktop account service.
Doesn’t work when unchecked: only connect when client is running on network authentication…, set on ALL farm machines, restart desktop services.
ANYWHERE on the connection GATEWAY-BROKER-TEMINAL is a bug with the involvement of the protocol NLA or something else, but LOGON when using a farm gateway (the role of the gateway + broker + Web RD on one machine) – NO! I.e. once you check the box: user must change password at next login, you no longer get logon and therefore cannot change user password!!!
Who knows where to dig in the GATEWAY-BROKER-TEMINAL bundle, somewhere in the innards of the protocol, somewhere in the policies or somewhere else?
Translated with http://www.DeepL.com/Translator (free version)
In short! Here’s the solution!
1. Make an account that will not be in any group of the domain, or rather make the group empty and put it the main user, removing even from the group domain users.
2. We add this user to the remote desktop group on the farm gateway only.
3. Then we write in ANY client properties of this user together with login, password, domain, ONLY in the gateway section.
4. In the same connection settings write the PC (usually the 1st PC in the farm), which needs to connect.
Everything. Profit. Thank you all. The solution was found by the collective mind of my team, for which she and I, including a BIG THANK YOU!
Anyone have any other methods to accomplish this reset without disabling NLA?
mstsc /v:server /remoteGuard
this also may not allow the user to connect but it should be possible to change the password beforehand
independent of the RDP security level
Hello Marek! How and where do I ADD this config?
Thanks!
Hi
This is not a config, this is command from command line to RDP (mstsc.exe is a MicroSoft terminal service client)
This worked — yeah!
mstsc /v:server /remoteGuard
I was able to change the password of a local admin account remotely using this (That local admin account had the attribute “require password change on next logon” enabled).
When only changing the logon user name in the MSTSC remote desktop client, remote logon attempts failed with an error message “password for this account is expired”, without offering me to change the password on logon through remote desktop.
Now since it is possible to perform that change password during logon with MSTSC in the above fashion, the behaviour of Windows seems quite non-sensical. Why does mstsc need such an awkward, mostly undocumented approach ?
The solution for the Client side by adding a line on the rdp file worked fine for me!!!
I need to change the password on first logon. It is working very well in Windows but there is no such option in Mac. How to enable it in Mac also?
Pingback: Cannot Rdp Until Local Login
Thank you for sharing such valuable information! This was really helpful and informative. I appreciate the time and effort you put into this. Keep up the great work!
https://mukhost.com/